Discreet Edge is a unique patent-pending technology that revolutionizes key management for the purposes of
cyber security and data privacy


Mitigation of the unsolved problem of insider threats

A proprietary solution for a new generation of data privacy requirements.

Cost-effective, scalable to millions of users/devices in the realm of IoT.

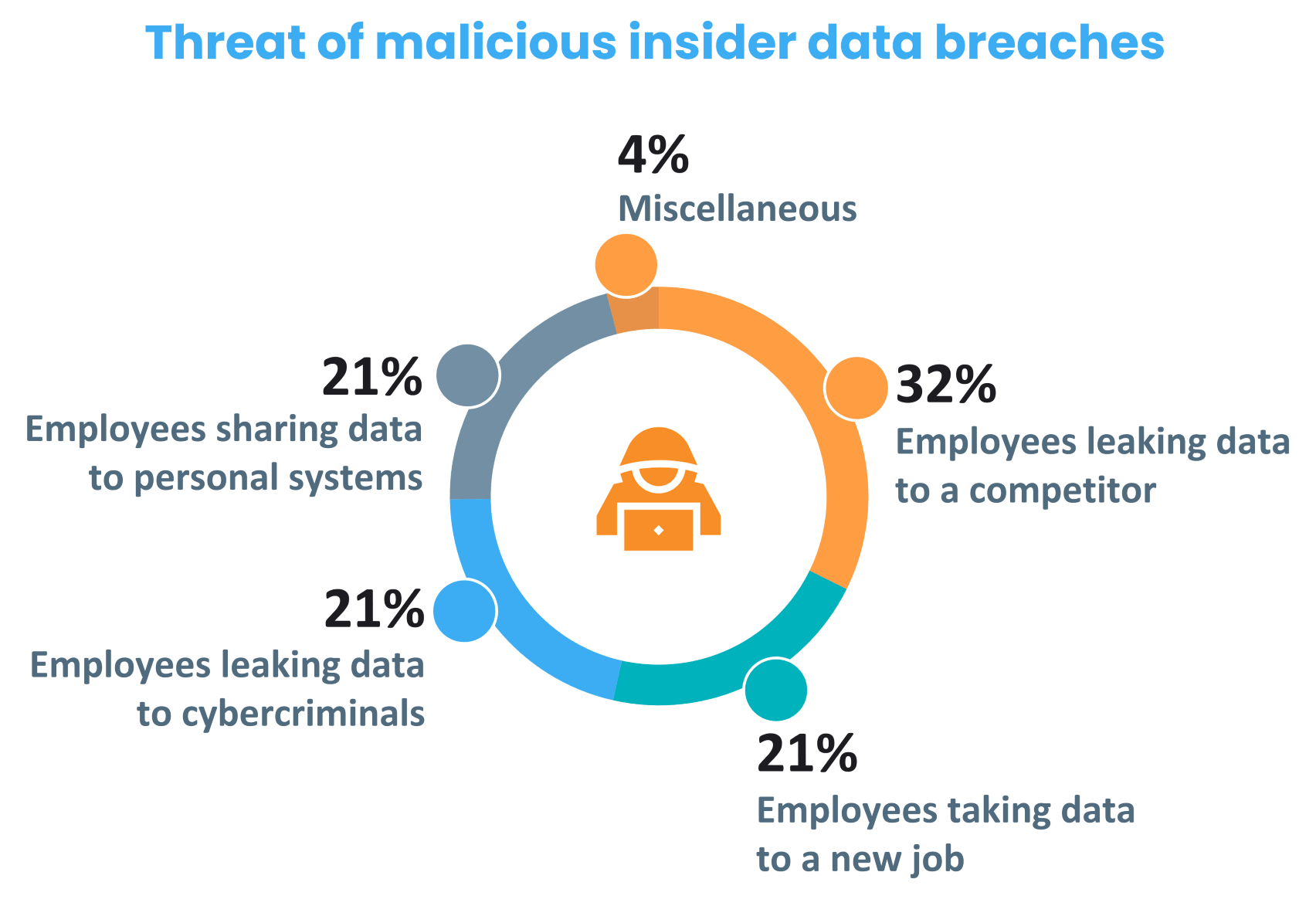
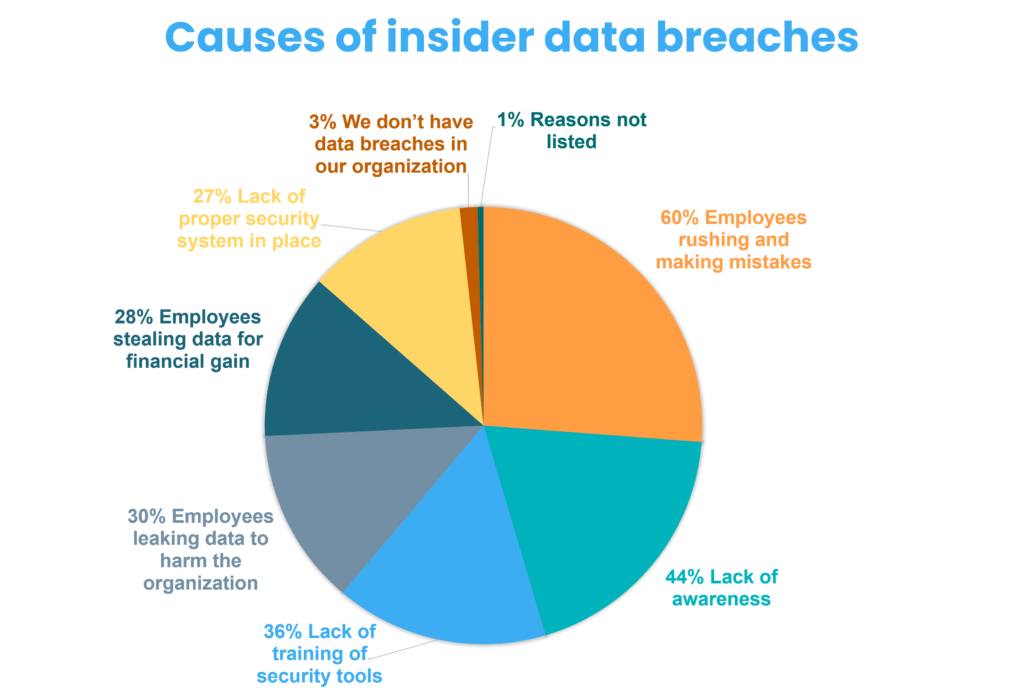
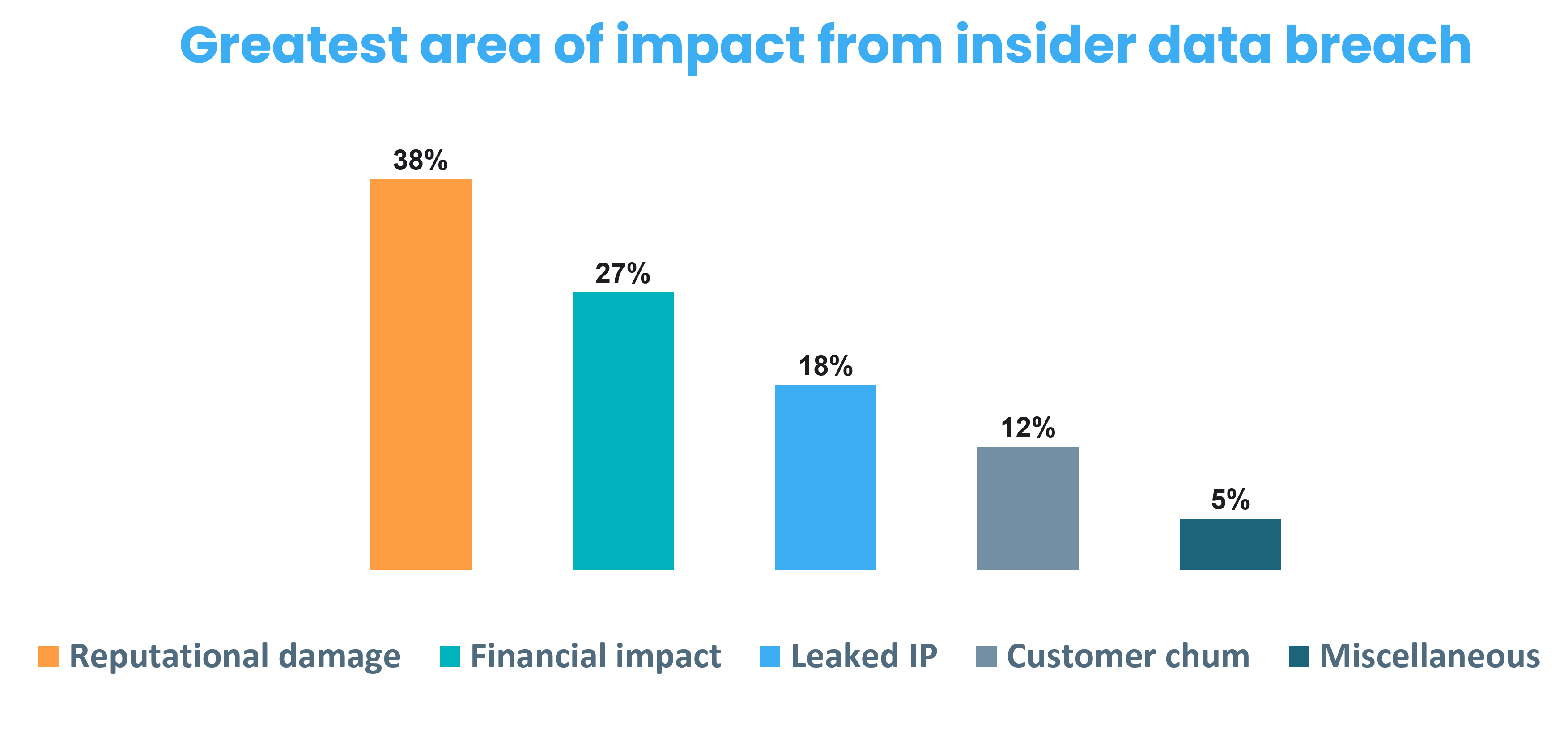
The two main actors in data breach:
Businesses in the US encounter about 2,500 internal security breaches daily.
66% of organizations consider malicious insider attacks or accidental breaches more likely than external attacks.
Over the last two years, the number of insider incidents has increased by 47%.
The cost of insider threats (related to credential theft) for organizations in 2020 is $2.79 million.
Insider threat stats reveal that more than 70% of attacks are not reported externally.
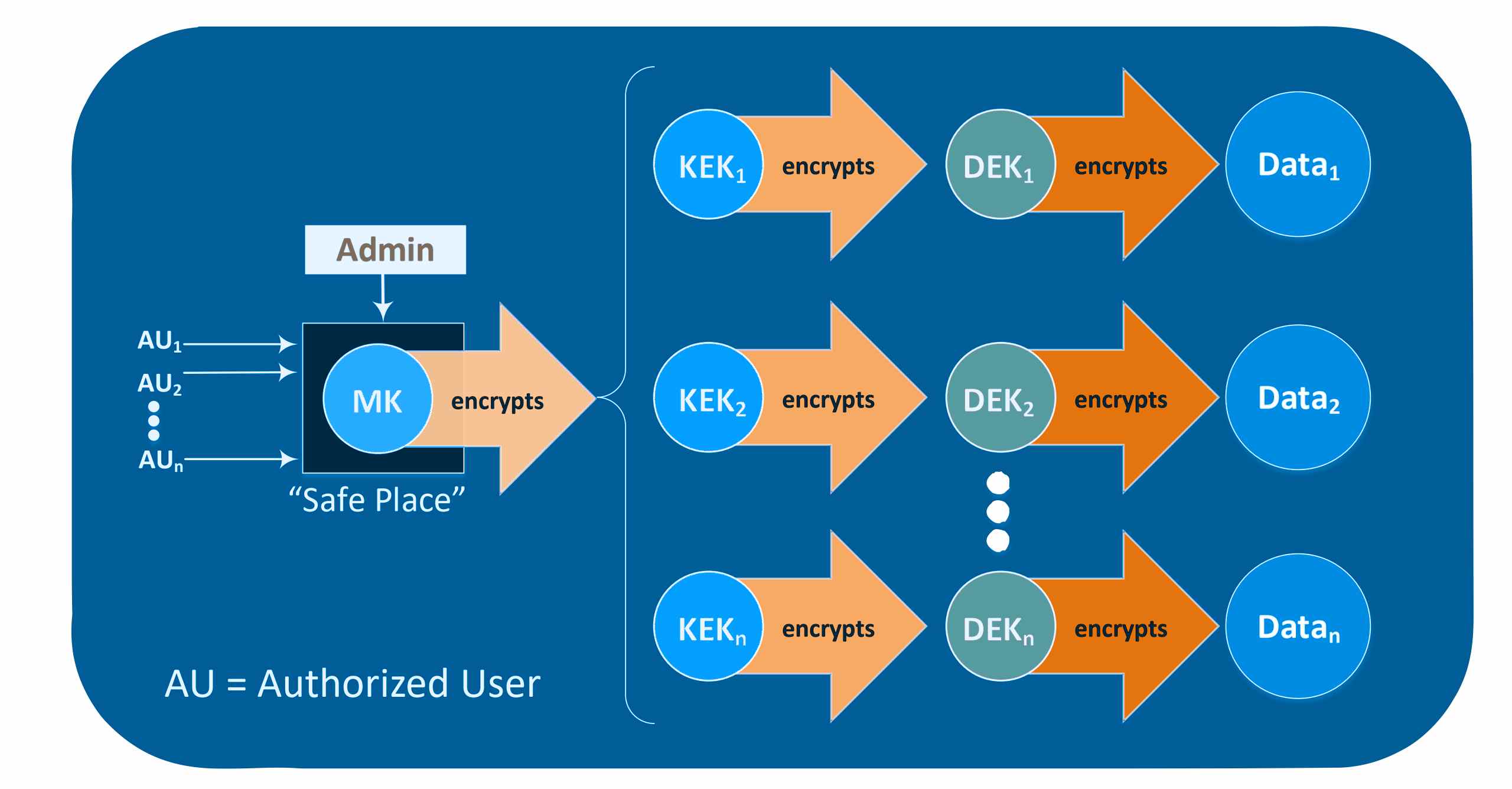
Leakage of Master Key can compromise the security of the entire data
Extremely cumbersome and error-prone SOPs
Very heavy reliance on manual checks and balances – human factors
Very high learning curve – scarcity of trained human resources
Heavy reliance on logging and audit – many a times the problem is detected after-the-fact

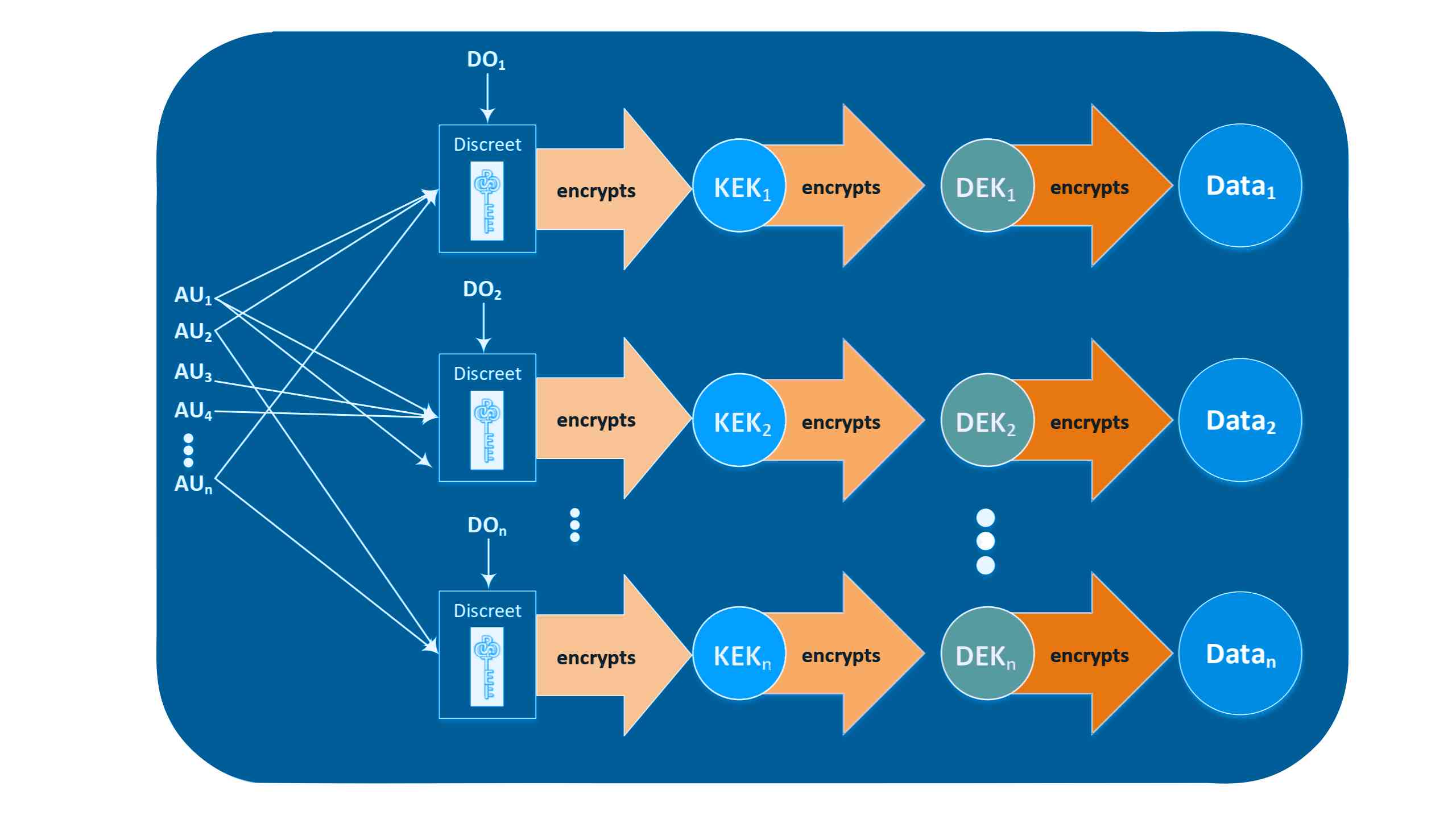
No single Master Key needs to be protected through obfuscation
All keys are secured through encryption – not through hiding/obscurity
Data Owner can be any trusted member of the team and is not required to have any technical skills
Access to each data set (segmented data) is controlled by different data owner (DO)
Keys are accessible to all authorized users
Keys are not accessible to any unauthorized user, including system administrators
Keys cannot be reverse-engineered
Effective protection against the unaddressed challenge of insider threats
Fraction of the cost of current solutions
Backup without fear of leakage
Simple disaster recovery

Simplified SOPs
Very low reliance on manual checks and balances
Very low reliance on logging and audit
Easier to learn – Availability of trained human resources

Enterprise Data Security
Automotive (Autonomous Vehicles)
Medical Devices
IoT/IIoT
FinTech
Blockchain
Crypto Wallets
Zero Knowledge


Coming Soon

Coming Soon
Get the most comprehensive data security solution in the world today!