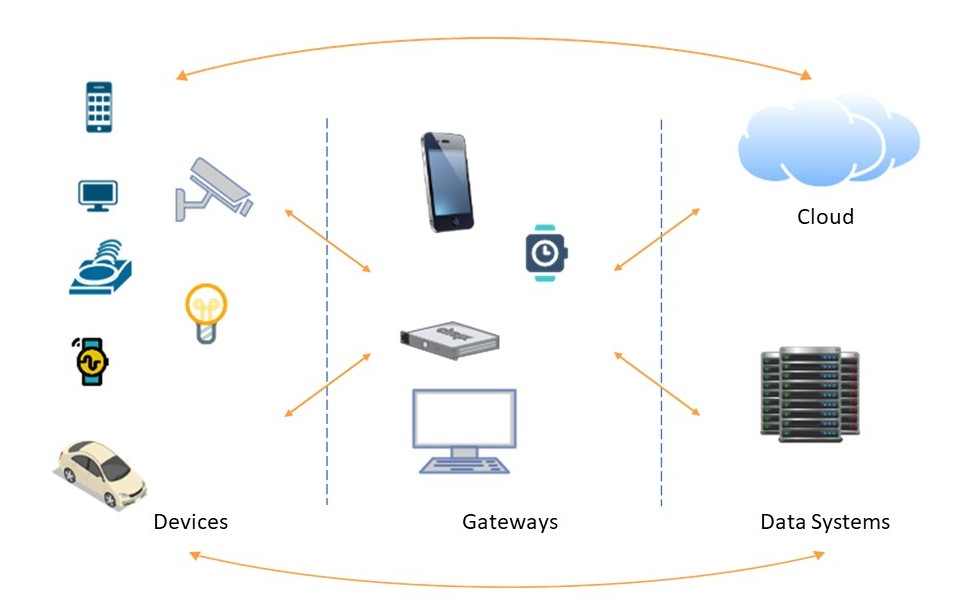
Devices:
Shopping cart
Mobile phones
Televisions
Smart watches
Data Systems:
AWS
Alibaba Cloud
Google Cloud Platform
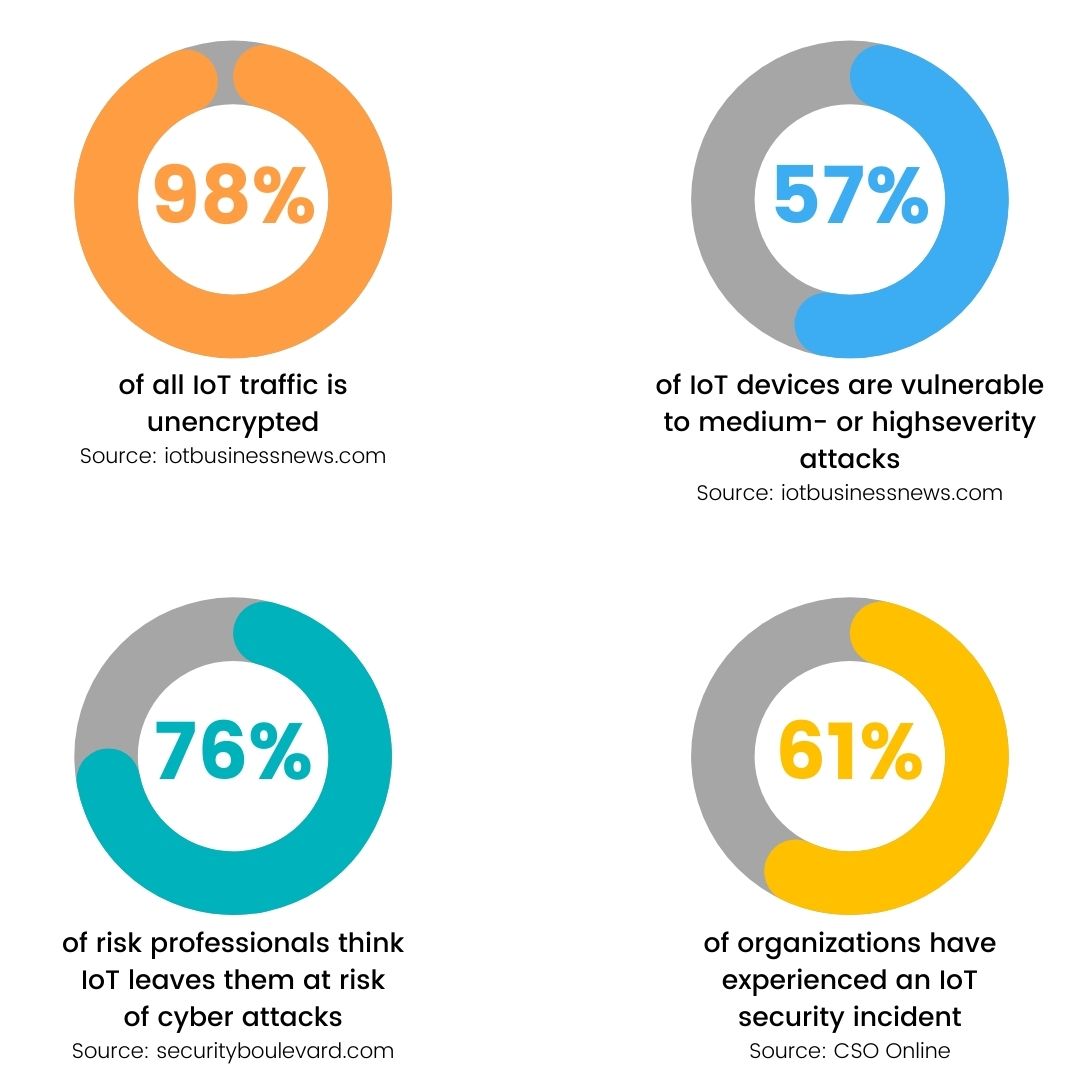
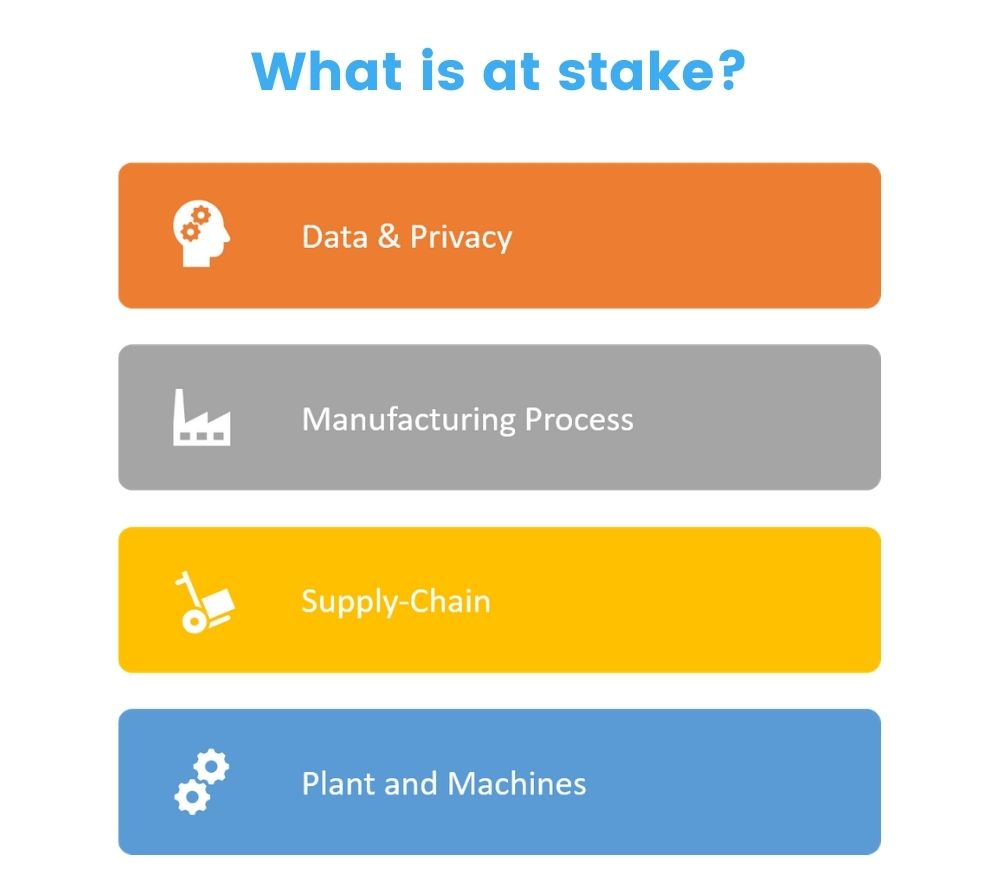
Insufficient privacy protection—failure to protect private information that is stored on the device and connected ecosystems.
Insecure data transfer and storage—such as the lack of access control and encryption during the movement of data.
Lack of device management—on devices deployed in production; results in poor security support.
Insecure default settings—the inability to fix insecure settings creates exploits in devices and systems.
Lack of physical hardening—creates a larger attack surface, which threat actors can leverage to take control of a device or system.
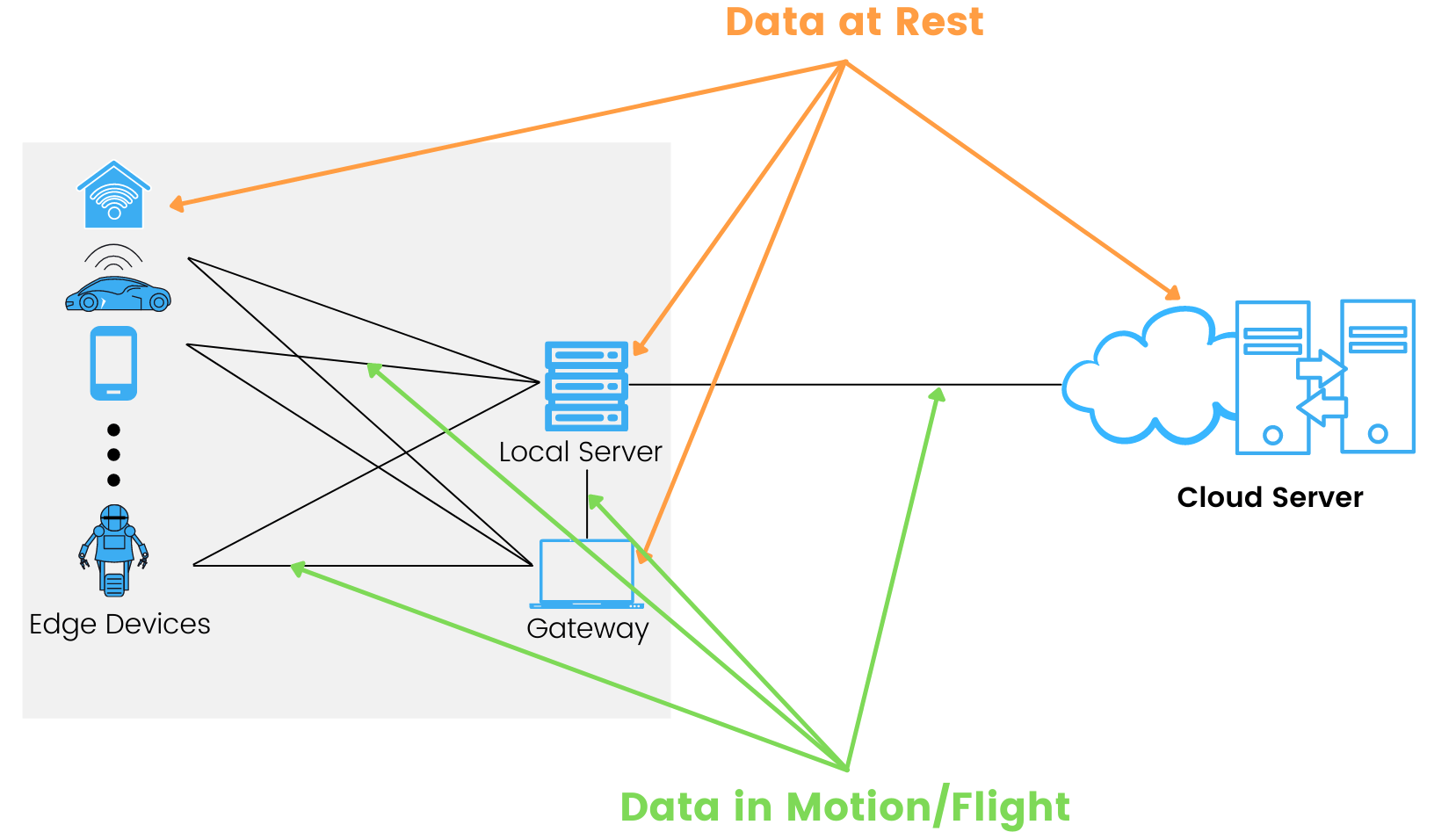

Market Differentiation of Discreet Edge’s solution over other Internet of Things (IoT) solutions:
Market Differentiation of Discreet Edge’s solution over other Industrial Internet of Things (IIoT) solutions: