There are four different types of users supported by Discreet, each with different roles.
SAs are responsible for the following:
An AU is a user who is authorized to have access to the encryption keys corresponding to a Data Object Type (DOT).
DOTMs have the following privileges:
SOs have the following roles:
There are five fundamental steps to set up the discreet system.
These steps pertain to creating/registering the two basic entity types (DOTS and Users) and authorizing/enabling users to access encryption keys.
In order to demonstrate how Discreet works, let’s take an example of a hypothetical company ‘AxsKey Inc.’
The following is a fictitious organization chart for AxsKey Inc.
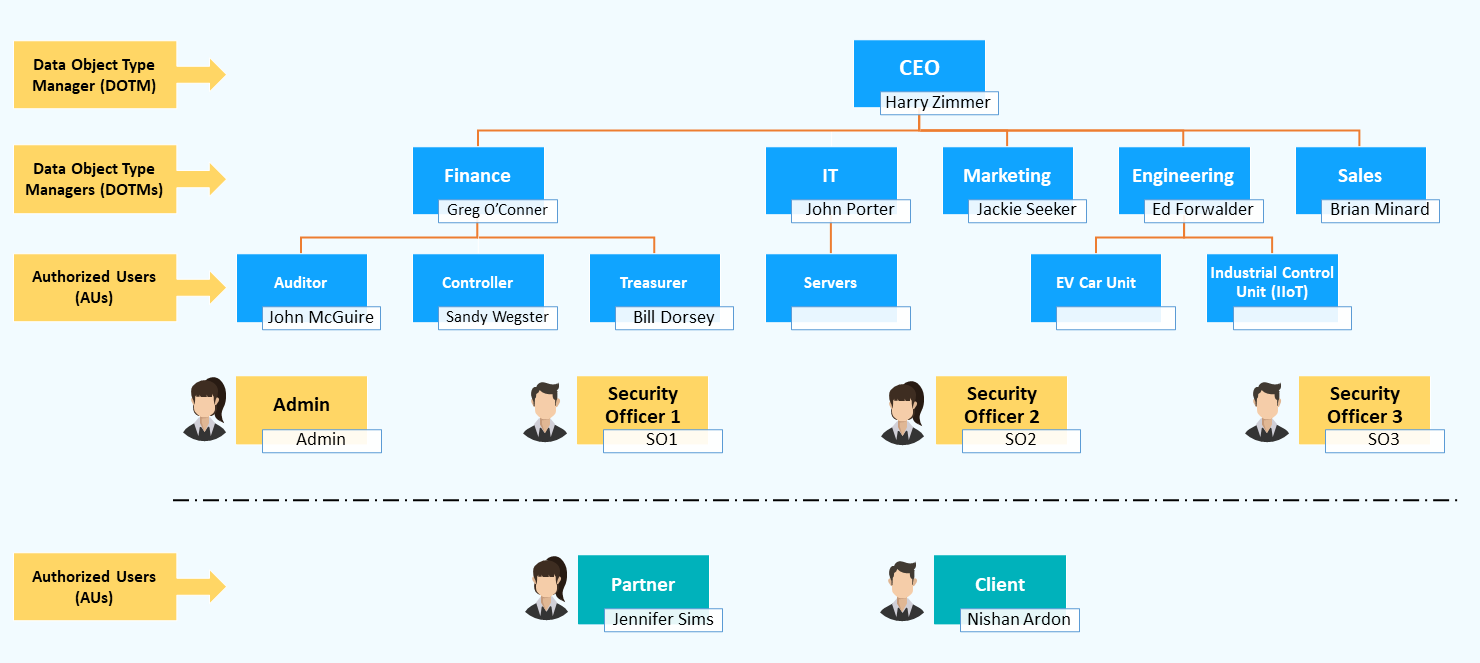
The four different types of users are shown on the above chart, as explained in Discreet User Types And Roles.
The following examples show how Discreet can be utilized:
There are two ways of uploading the assets:
A CEO and department head can provide DOTM or AU level access to their subordinates.
Department heads are assigned as DOTM for their respective departments, and they have the option to revoke or limit the CEO’s access to any asset under their department.
DOTM can then assign their subordinates as AU or DOTM as per the requirement.
In addition, DoTM can also provide cross-departmental access to other departments’ employees.
Authorized Users (AUs) can only access the folder/assets assigned to them by DOTM.
AUs cannot add any asset/folder, they can only view/edit the assets assigned to them by DOTM.
AU cannot also assign another user to their assets.
System Admin (SA) can create a client/partner account as AU.
The client/partner is then required to change the password to activate their account.
DOTM can share any asset with the client/partner providing them with Read or Write access.
The client/partner cannot share the asset with anyone else.
In case no authorized users of a DOT are available or if a user loses their login credentials, SOs can transfer the rights to another user or reset the password by following the necessary protocols.
One of the SO needs to log in and initiate the Reset User Password or Transfer Assets protocol. SO then assigns another SO to complete the protocol.
The second SO then logs in to their account and completes the process.
In case a SO is not reachable or if he/she has left the organization, the available SOs can assign another user as a SO by following the similar protocols as explained in the previous step.
SA – Discreet System Administrator
AU – Discreet Authorized User
DOTM – Discreet Data Object Type Manager
SO – Discreet Security Officer
DOT – Data Object Type
DEK – Data Encryption Keys
KEK – Key Encryption Keys